- Top
- Basic Policy on Information Security
Basic Policy on Information Security
Seven & i Holdings Co., Ltd. and its domestic subsidiaries (hereinafter “the Group” ) provide new value and services to customers focusing primarily on the convenience stores.
In providing these services, the Group recognizes that protecting customer information and other Group-held information assets from various threats, such as unauthorized access and cyberattacks, and ensuring Group-wide information security are the Group’s most critical management priorities.
The Group has established the “Basic Policy on Information Security” to leverage information assets and evolve into a corporate group that delivers significant value to society through digital strategies. The policy ensures that all executives, employees and parties involved in our business operations properly handle and appropriately utilize information assets.
Based on this policy, the Group will establish an information security management system, working to embed it across all executives and employees through education and training. Moreover , the Group is committed to implementing and continuously improving a management system that adapts to evolving environmental factors, including shifts in societal demands and cybersecurity advancements.
Last Updated: February 16, 2026
Seven & i Holdings Co., Ltd.
- 1Information Security Structure
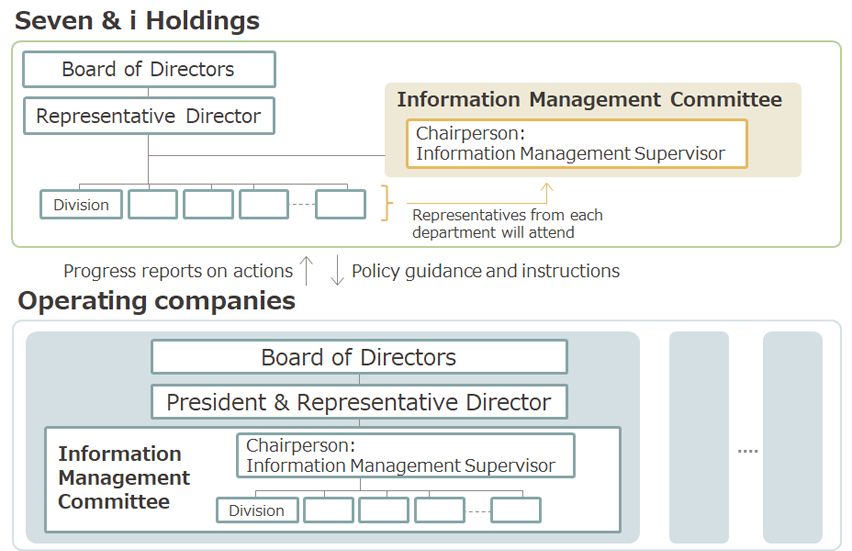
Seven & i Holdings Co., Ltd. supports the development of internal controls and assesses their effectiveness across all companies in the Group. Under the guidance of the Information Management Committee, the office strives to enhance and enforce the Group-wide information security.
Each Group company also designates an Information Management Supervisor responsible for overseeing information security planning, promotion, and management. Working under their respective Information Management Committees, these officers ensure the safety of important information, including confidential and personal information.
- 2Information Security Measures
- 1Compliance
The Group will comply with all applicable domestic and international laws, regulations, and contractual obligations regarding information security. Moreover, the Group strives to adhere to other relevant information security standards and guidelines.
Additionally, the Group will establish information security policies and regulations, to ensure the proper implementation of information security measures. - 2Information security management system
The Group will secure the necessary resources for information security measures and will continuously maintain and enhance its information security management system. - 3Management and protection of information assets
The Group will appropriately manage information security based on the risk assessment of information assets. All executives and employees will not utilize its information asset for any non-business purpose. - 4Human management
The Group will periodically educate and train all executives and employees to ensure comprehensive awareness of information security responsibilities, obligations and implications of non-compliance. - 5Physical access management
The Group will implement physical access controls, including locking, monitoring, and access restrictions commensurate with the importance of information assets , to protect them from threats such as intentional or accidental leakage, theft, falsification and destruction. - 6Technical management
The Group will implement technical measures including access control, system development, and operational management, to prevent, detect, and analyze information security incidents (e.g., leakage, falsification, loss, and destruction or impairment of data), arising from information system vulnerabilities. - 7Ensuring supply chain information security
The Group will assess the information security measures across its entire supply chain, including business partners and contractors, and require appropriate information security management. - 8Information security incident response
To prepare for information security incidents, the Group will establish response systems and procedures to ensure prompt and effective response in collaboration with internal and external stakeholders. Should an information security incident or a potentially related event occur, the Group will respond promptly and appropriately to minimize impact and prevent recurrence. - 9Ensuring information security in business continuity
In preparation for disasters or accidents, the Group will develop a business continuity plan, and ensure information security. - 10Sharing and effectively utilizing insights and intelligence related to information security
The Group will participate in information security sharing initiatives, exchanging insights and intelligence. Moreover, the Group will establish an environment to effectively utilize it. - 11Inspection and audit
The Group will conduct periodic and ad-hoc inspections and audits to validate compliance with information security policies and assess the validity and efficacy of implemented security measures. Where deficiencies are found, the Group will implement corrective actions. - 12Continuous improvement
The Group will continuously make improvements to maintain and enhance its information security management system and security measures.
- 1Compliance
- 3Enhancement of Cyber Security Measures
Recognizing cyberattacks as a significant management risk due to their daily escalation in sophistication and complexity, the Group will strive to enhance cybersecurity measures by implementing a multi-layered defense, such as protection against unauthorized network intrusions and appropriate access control, along with establishing response systems to effectively counter diverse threats.
- 1Establishment of a dedicated organization
The Group has established a dedicated cybersecurity organization, striving to enhance cybersecurity measures to prevent security incidents, including reviewing the security of its information systems and operations, conducting third-party vulnerability assessments, monitoring for unauthorized access, and responding to identified vulnerabilities. - 2Education and training
To ensure prompt response and minimize damage should a cyberattack or similar incident occur, the Group will conduct regular education and training focused on cybersecurity incidents for its dedicated cybersecurity organization, executives, and employees, to empower their readiness and operational effectiveness. - 3Cooperation with external organizations
The Group will cooperate with external organizations, including JPCERT/CC and NCA (Nippon CSIRT Association), to share cyber threat intelligence and countermeasure trends, to promptly respond to cyberattacks.
- 1Establishment of a dedicated organization
