- Top
- Basic Policy on Information Security
Basic Policy on Information Security
Seven & i Holdings Co., Ltd. and its domestic subsidiaries (the “Group” or “we”) provide new value and services to customers through a variety of business types such as convenience stores, superstores, department stores, specialty stores and financial services and e-commerce.
In providing these services, we recognize that the most important management issue is protecting customer information and other information assets held by the Group from various threats, such as unauthorized access and cyberattacks, and ensuring the information security of the entire Group.
The Group has established the Basic Policy on Information Security to ensure that officers, employees and all of those who are involved in our business operations properly deal with and appropriately use the information assets, in order for us to actively use the information assets and develop into a company group that has value to society through digital strategies.
Based on this Basic Policy, we will establish an information security management system and make efforts to instill it into all officers and employees through education and training, and also build and continuously improve a management system according to environmental changes due to social demands, cybersecurity or the like.
Revised on April 1, 2023
Seven & i Holdings Co., Ltd.
President and Representative Director Ryuichi Isaka
- 1Structure for Information Security
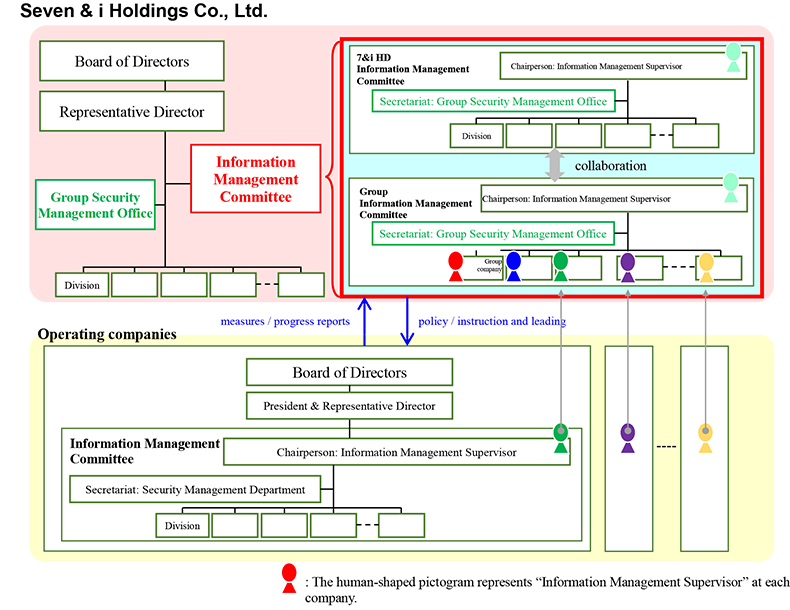
The Group established the Group Security Management Office as an organization directly reporting to the Company’s Representative Director, supports the establishment of an environment of control and evaluates its control system on each Group company and strives to enhance and ensure information security among the entire Group under the Information Management Committee.
Moreover, each Group company appoints an Information Management Supervisor in order to supervise planning, promotion and management related to information security, and ensure the safety of material information including confidential or personal information under the each Company’s Information Management Committee.
- 2Information Security Initiatives
- 1Compliance
The Group shall be compliant with domestic and foreign laws, regulations, restrictions and contractual obligations which apply to it regarding information security, and also strive for compliance with other standards and guidelines related to information security.
The Group shall also establish information security rules to properly implement information security measures. - 2Structure for information security management
The Group shall secure the resources necessary for information security measures and strive to maintain and improve its information security management system. - 3Management and protection of information assets
The Group shall appropriately manage information security based on the risk assessment of information assets. Moreover, the officers and employees of the Group shall not use its information assets other than for the business purpose for any reason. - 4Human management
The Group shall periodically educate and train its officers and employees to ensure and raise their awareness of their responsibilities, obligations and penalties for information security. - 5Physical access management
The Group shall implement physical access controls, such as locking, monitoring, and access restrictions, depending on the importance of information assets, in order to protect the information assets from threats such as intentional or negligent leakage, theft, falsification and destruction. - 6Technical management
The Group shall conduct technical measures, such as prevention, detection and analysis of any leakage, falsification, loss and destruction of, and damage to, information caused by vulnerability of information systems such as vulnerabilities in access control, development and operation management of information systems. - 7Ensuring information security of the entire supply chain, including business partners and contractors
The Group shall strive to understand the information security environment of the entire supply chain, including business partners and contractors, and require appropriate information security management. - 8Response to information security incidents and accidents
The Group shall establish structures and procedures, in preparation for information security incidents and accidents, in order to promptly conduct effective countermeasures in cooperation with the relevant parties of inside and outside the Group. The Group shall also respond promptly and appropriately to minimize damage and prevent the recurrence of any information security incident or accident, or an event that may lead to such an incident or accident. - 9Ensuring information security in business continuity
The Group shall establish a business continuity plan for disaster or accident, and strive to ensure information security. - 10Obtaining, providing and effectively utilizing intelligence related to information security
The Group shall participate in intelligence and knowledge sharing activities related to information security, and actively obtain and provide intelligence and knowledge. The Group shall also establish an environment to use the intelligence and knowledge gathered effectively. - 11Inspection and audit
The Group shall conduct inspections and audits on a regular basis or on demand to verify that the information security rules are being complied with and that information security measures are appropriate and effective. The Group shall also take corrective action when any problems are detected. - 12Continuous improvement
The Group shall continuously make improvements to maintain and enhance its information security management structure and security measures.
- 1Compliance
- 3Enhancement of Cyber Security Measures
The Group considers that cyberattacks, which are getting more sophisticated and complicated every day, should be a material management risk, and shall strive to build its cyber security measures by building a defense in depth including protection against unauthorized network intrusions and appropriate access control, as well as a structure capable to respond to threats.
- 1Establishment of a professional organization
The Group has established a professional organization responsible for cyber security to review the security of its information systems and their operations. The Group shall also strive to improve its cyber security measures to prevent security incidents, such as having vulnerability assessments conducted by a third-party institution, monitoring unauthorized access and responding to vulnerabilities. - 2Education and training
The Group shall conduct education and training to prepare against anticipated cyber security incidents or accidents at ordinary times, in order to respond quickly to cyberattacks and minimize their damage, and shall strive to improve the response capabilities of the professional organization, officers and employees so that its structure for response for incidents and accidents can work effectively. - 3Cooperation with external organizations
The Group shall cooperate with external organizations, including JPCERT/CC and NCA (Nippon CSIRT Association), to share intelligence and knowledge related to cyberattacks and countermeasure trends so that it can quickly respond to cyberattacks.
- 1Establishment of a professional organization
